OASIS Interoperability Demos at RSA 2010
OASIS Security Standards Interoperability Demo Showcase: XSPA, IMI, KMIP
An OASIS Security Standards Interoperability Demo Showcase was planned for the RSA 2010 (March 1-5, 2010, Moscone Center, San Francisco, California), OASIS Booth 2545.
Members of OASIS showcase interoperable products that support security standards, including Cross-Enterprise Security and Privacy Authorization (XSPA), Identity Metasystem Interoperability (IMI), and Key Management Interoperability Protocol (KMIP). Demo participants [were scheduled to] include: CA, Inc., General Services Administration, Hewlett Packard, IBM, Information Card Foundation, Jericho Systems, Microsoft, Novell, SafeNet, Inc., Sun Microsystems, U.S. Department of Defense, U.S. Department of Veterans Affairs.
The following interoperability demonstrations were planned:
- Cross-Enterprise Security and Privacy Authorization (XSPA) Demonstration
- Identity Metasystem Interoperability (IMI) Demonstration
- Key Management Interoperability Protocol (KMIP) Demonstration
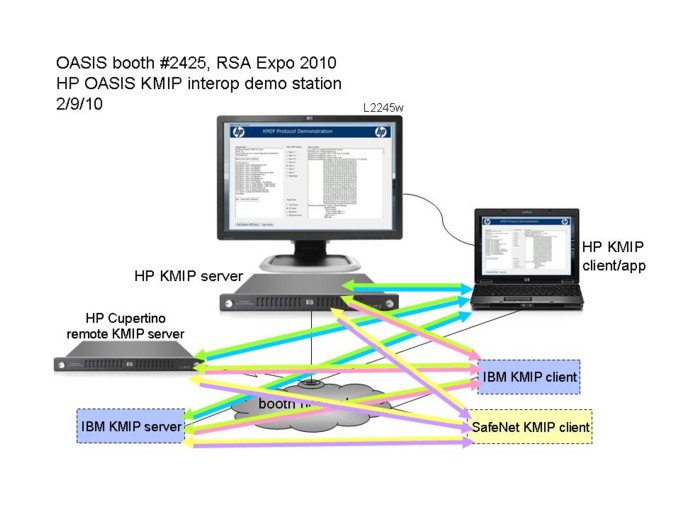
Key Management Interoperability Protocol (KMIP) Demonstration: "The OASIS Key Management Interoperability Protocol (KMIP) V1.0 specification for interoperable communication will be demonstrated in the OASIS Interop Showcase at the RSA Conference and Exposition 2010. The KMIP interop demonstration will show client programs implemented by HP, IBM, and Safenet using the KMIP v1.0 protocol, and communicating securely with key management servers implemented by HP and IBM. The clients and servers will demonstrate essential key management use cases such as generating cryptographic keys, locating existing keys, retrieving, registering, and deleting keys. This OASIS KMIP demo provides an excellent opportunity for vendors and end-users to see KMIP in practice, demonstrating the value of a standard comprehensive protocol for enterprise key management operations in multi-vendor environments."
The KMIP interoperability demonstration will consist of a number of client-to-server scenarios, each made up of multiple protocol message exchanges. The clients will connect to the key management servers using KMIP and exercise a number of protocol operations, object and attributes.
The scenarios are as follows (using use cases from the KMIP Use Cases document):
- Request for the creation of a symmetric key on the server and subsequent destruction of the created key.
- Registration of a template, which can be used to facilitate the creation of objects with similar properties. Using the registered template, a client creates a symmetric key and gets the attribute values for the key (the key metadata). Finally, the key is destroyed.
- A key is created and a Name attribute is specified. A subsequent request to the server is made to locate the unique identifier of the created key based on the name. The key is then retrieved using a Get operation, and the key is finally destroyed.
- Registration of a template and the creation of a key based on that template. Modification of the key metadata.
- Demonstration of the asynchronous functionality supported by the protocol, where the client needs to poll the server until an operation finishes.
- Registration of a third-party key (or a key generated locally by the client) to the server.
Identity Metasystem Interoperability (IMI) Demonstration: "The OASIS Identity Metasystem (IMI) V1.0 specification and the profile developed by the US Government (GSA/ICAM) will be demonstrated in the OASIS Interop Showcase at the RSA Conference and Exposition 2010. The IMI interop demonstration will show relying party software implemented by CA, Microsoft, and Novel using the IMI v1.0 protocol, in accordance with the US Government profile. Multiple Information Card Foundation (ICF) members will also be issuing IMI based cards during the demonstration. Card selector software from Microsoft and others will be used to provide users access to a number of government sites with commercially issued identities using the ICAM profile of IMI 1.0."
Cross-Enterprise Security and Privacy Authorization (XSPA) Demonstration: "The purpose of the TC is to specify sets of stable open OASIS standards and interoperability profiles, and create other standards or profiles as needed, to support secure and private exchange of healthcare information. Work to date supports and has been accepted by the US Department of Health and Human Services Health Information Technology Standards Panel (HITSP) Access Control Transaction Package specification TP20, including access control capabilities required to support the HITSP Manage Consent Directive Package specification TP30. This includes the exchange of access control decision information such as requestor identity, role data, location that can be used by healthcare providers to enforce permitted operations on resources and associated conditions and obligations. The OASIS standards and profiles provide advanced security, privacy and integrity of sensitive patient data end to end."
References
Prepared by Robin Cover for The XML Cover Pages archive.